Research
Next-Generation Information Security Lab (NISL) studies security of communication and networks, blockchain technology, post-quantum cryptography, vehicle ad-hoc networks, e-commerce and so on. There cryptographic researches guarantee confidentiality, integrity, availability of information.
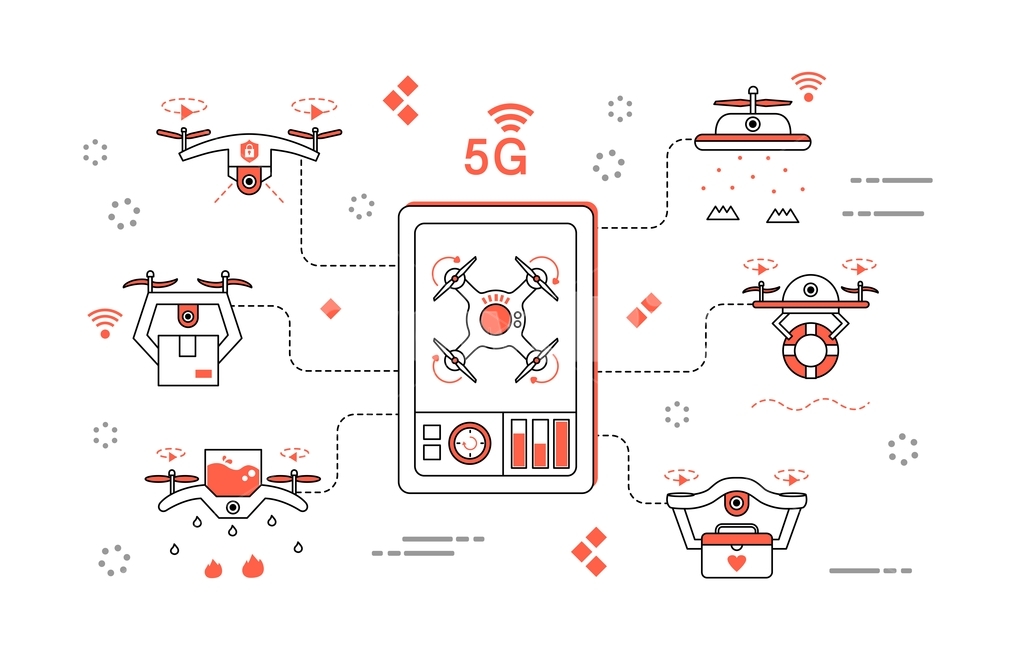
Security of unmanned vehicle (무인이동체 보안)
An unmanned vehicle is a mobile vehicle that operates autonomously, which does not have an operator on board. With its own computing system, unmanned vehicle interacts external environments and performs its services, including delivery, relief, exploration. However, an attacker can pose a threat to the network by collecting sensitive information through the data from these wireless channels. We study the data integrity, confidentialiy, and mutual authentication suitable for unmanned vehicle environments.

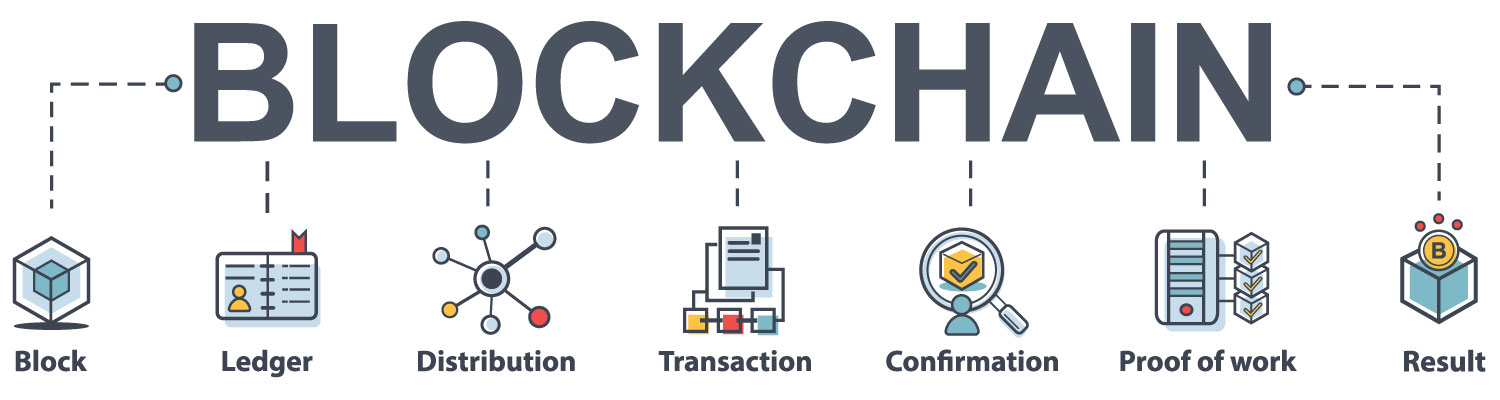
Blockchain Technology (블록체인 기술)
A blockchain is a decentralized ledger of all transaction across a P2P(Peer to Peer) network. The innovation of this technology is that participants transfer assets or data through the internet without the need for a trusted third party. This mechanism of blockchain can be applicable for financial services, voting, cloud service, healthcare, automotive energy management and many other fields. We study the security system and cryptographic techniques using the blockchain.
Post-quantum Cryptography (양자 후 암호)
The quantum computer will break today's public-key cryptosystem such as RSA and ECC using Shor and Grover algorithm. A post-quantum cryptosystem is secure cryptosystem even if an attacker has a large quantum computer and try to attack the system. Today, several post quantum cryptosystems have been proposed for preventing quantum computing attacks, including hash based, multivariate, code based and lattice based cryptosystem. We study the post quantum cryptosystem for improving security and efficiency.
Security of IoT (사물인터넷 보안)
The concept of Internet of Things (IoT) is that every object in the Internet infrastructure is inter connected into a global dynamic expanding network. Sensors and smart objects are classical computing devices key parties of the IOT. The computing performance of those devices are comparatively low, hence, it is hard to apply traditional cryptographic technologies. We study user authentication and key management suitable for IoT environments.
Security of Vehicular Ad-hoc Networks (차량 보안)
Vehicular Ad-Hoc Networks (VANETs) are distributed, self-organized networks built up by many high-speed vehicles. All vehicles in the network would install onboard units (OBU), which would integrate the vehicles’ wireless communications, micro-sensors, embedded systems, and Global Positioning System (GPS). These smart vehicles could then communicate with each other as well as with roadside units (RSU), such as traffic lights or traffic signs, which would then improve the driving experience and make driving safer. Despite these advantages, VANETs come with their own set of challenges, particularly in the aspects of security and privacy. Lack of authenticated information shared in the network may lead to malicious attacks and service abuses, which could pose great threats to drivers. We study authentication and key distribution between vehicles and RSUs.
Security of FinTech (핀테크 보안)
FinTech (Financial Technology) is defined as the technique to create efficient financial services using IT technologies. FinTech is an innovative technology through IT platform and big data, and is expected to improve the security and solve problems of the conventional banking system. Financial institutions has introduced the technologies and investment in order to provide safe and effective services to users, such as Samsung pay and Apple pay. However, In the financial environment, information disclosure and security incident has occurred so they has lost the trust from their customers. Moreover new variant of the security threats and attack techniques have occurred. We study user identification, non-repudiation, integrity and confidentiality of data for secure user authentication.

